With the current advancements in the networking fields, the sharing of data and information takes the most important role, and network security is responsible for maintaining data safety during transmission. In this tutorial on ‘what is a Proxy’, you will be looking into one such aspect of network security for our data and system.
What Is a Proxy?
A proxy is a way to access information on the internet using a different IP address assigned to the system when connected to a proxy server.
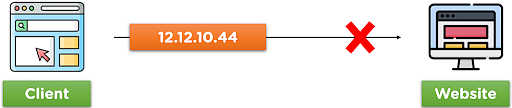
For example, say that you want to access a website, but because of some reasons, your system is unable to access the site. The issue here arises due to your IP address and the security reasons of that particular website.
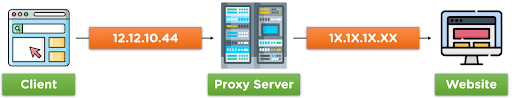
But using a proxy, you can mask our original IP address and access the site using a different IP address allowed by the targeted website.
What Is a Proxy Server?
The proxy server is a network system designed to work as an intermediary between the client's request and the targeted website or internet resource requested by the user.
The proxy server provides its user with the following functions:
- Network Security and protection against cyberattacks, for this function as the name, suggests the proxy provides its users with data security being accessed and protects the system from cyber attacks such as hacking attempts.
- Network Proxy for data and internet resources, when you access the internet to search for some sensitive information, the proxy acts as a mask for your original IP address. It hides it with an IP address assigned by the proxy server.
Next, in the tutorial on ‘what is a Proxy?’, you will look into the working of the proxy server.
Why Use Proxy?

Now using proxy services, you can avail several beneficial services, some of which are as follows:
- Prevention against cybercrimes - The proxy service provides user protection against hacking attempts. It prevents attackers from accessing the IP address data by issuing a proxy IP address to the client’s IP address.
- Request Security - The proxy service also encrypts the user’s information request to prevent it from being accessed by potential threats.
- High-Speed and Less Bandwidth - When accessing data through the proxy, the proxy servers cache the information accessed by the user. This is done to provide high-speed data access to the data using the cache file for a repeated request.
The Workings of the Proxy Server
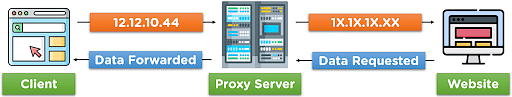
When the client requests a particular data or access to a website, the request is directed to the proxy server for the initial step. Then the proxy sends the access request to the targeted website on the client’s behalf.
The proxy server alters our original IP address to prevent any cyber-attacks and provide protection against internet resources.
Types of Proxy Servers
Depending on the client’s request or service to be provided, you can divide the proxy into different formats, some of which are:
- Forward Proxy server - In this proxy server, the user’s request is passed from the internal server to the internet by passing through a firewall check. The firewall is configured to deny or allow the client’s request, depending on the data or website to access.
- Anonymous Proxy Server - This proxy server is not configured to hide the user’s IP address. Instead, it provides it with the anonymous status for the client system.
- Transparent Proxy Server - This proxy server provides information hiding services to the client. This proxy server may hide a particular part of the user data, and the remaining data is still accessible on the internet.
- HTTP Proxy - These proxy servers are designed to save the cache data of the websites and the information accessed by the user. This step improves the performance and store access time when the user revisits the cached website or data.
Disadvantages of Using Proxy
- Logging Client Request - Many proxy servers, as you understood earlier in the tutorial, are configured to save the user's IP address and the requests made by the users for future reference, but this, in turn, sabotages the user's privacy.
- Free Proxy Services - Using free proxy services available on the internet may do more harm than good to the user’s sensitive data and the web requests done by the proxy service.
- Applying Encryption - It is important to check whether the proxy server is applying proper encryption to the client’s network data and the information requested by the user.
Grab the opportunity to be a part of the MIT CSAIL Professional Programs community and interact with your peers. Attend masterclasses from MIT faculty in our PGP in Cyber Security and expedite your cybersecurity career in no time!
Conclusion
In this tutorial on ‘what is a Proxy?’, you looked into the information regarding proxy services. You learned about the functions provided by the proxy server to its user to access data and information on the internet without compromising any sensitive data and preventing cyber attacks.
If you want to learn more about the working of a proxy and the service provided by a proxy server, you can refer to Simplilearn’s Cyber Security Expert course. This expert course will help you to understand the inner workings of the proxy server and the functioning of its services.
Do you have any questions related to this tutorial on ‘what is a Proxy?’ If yes, feel free to mention them in the comment section at the bottom of this page. Our team will help you solve your queries ASAP.
